This is a simple example of how to setup Ansible Tower to automate a Cisco IOS Router. This post is written from a network engineer’s perspective.
NOTE: Only tested with Ansible Tower 3.1.3 which uses Ansible 2.3 at the time this post was written
Topology
The example setup was done in GNS3 using the Cisco ViRL IOS image and a RHEL 7.3 VM with a valid subscription(license). Details of how this was done will be discussed in a future blog post.

Installing Ansible Tower
Follow the Ansible Tower installation steps. This demo uses the default account of admin.
Create a Test Playbook.
A test playbook called test-network-automation can be found on Github. It contains one playbook called test.yml, that runs show version on the IOS router.
test.yml
---
- hosts: switches
connection: local
vars:
cli:
host: ""
username: ""
password: ""
tasks:
- name: run show version
ios_command:
commands: "show version"
provider: ""
register: show_version
- name: print the show version output
debug: var=show_version
Configure the switch.
Here is the relevant IOS configuration
ip domain-name linuxsimba.local
!--- Generate an SSH key to be used with SSH.
crypto key generate rsa
ip ssh time-out 60
ip ssh authentication-retries 2
ip ssh version 2
username ansible privilege 15 password 0 1q2w3e4r5t!
rtr01#show ip ssh
SSH Enabled - version 1.99
Authentication methods:publickey,keyboard-interactive,password
Authentication Publickey Algorithms:x509v3-ssh-rsa,ssh-rsa
Ansible Tower Configuration Workflow
The Ansible Tower setup to configure network automation can be summarized in the following flow chart
Configure a Project
Add the test playbook into the Tower database. This is done by creating a Project

Configure an Empty Machine Credential
Because the connection made to the IOS device is made via a proxy connection on the Ansible tower server, all one has to do is create an empty machine credential. That is, just give the credential a name. For this example, because Ansible Vault is used , the Vault password is filled out. The Vault Password is tower. It is good practise to encrypt your network authentication. Tower does provide a feature called Network Credentials but it will not be covered on this post. The method of encrypting network authentication information within the playbook was preferred.

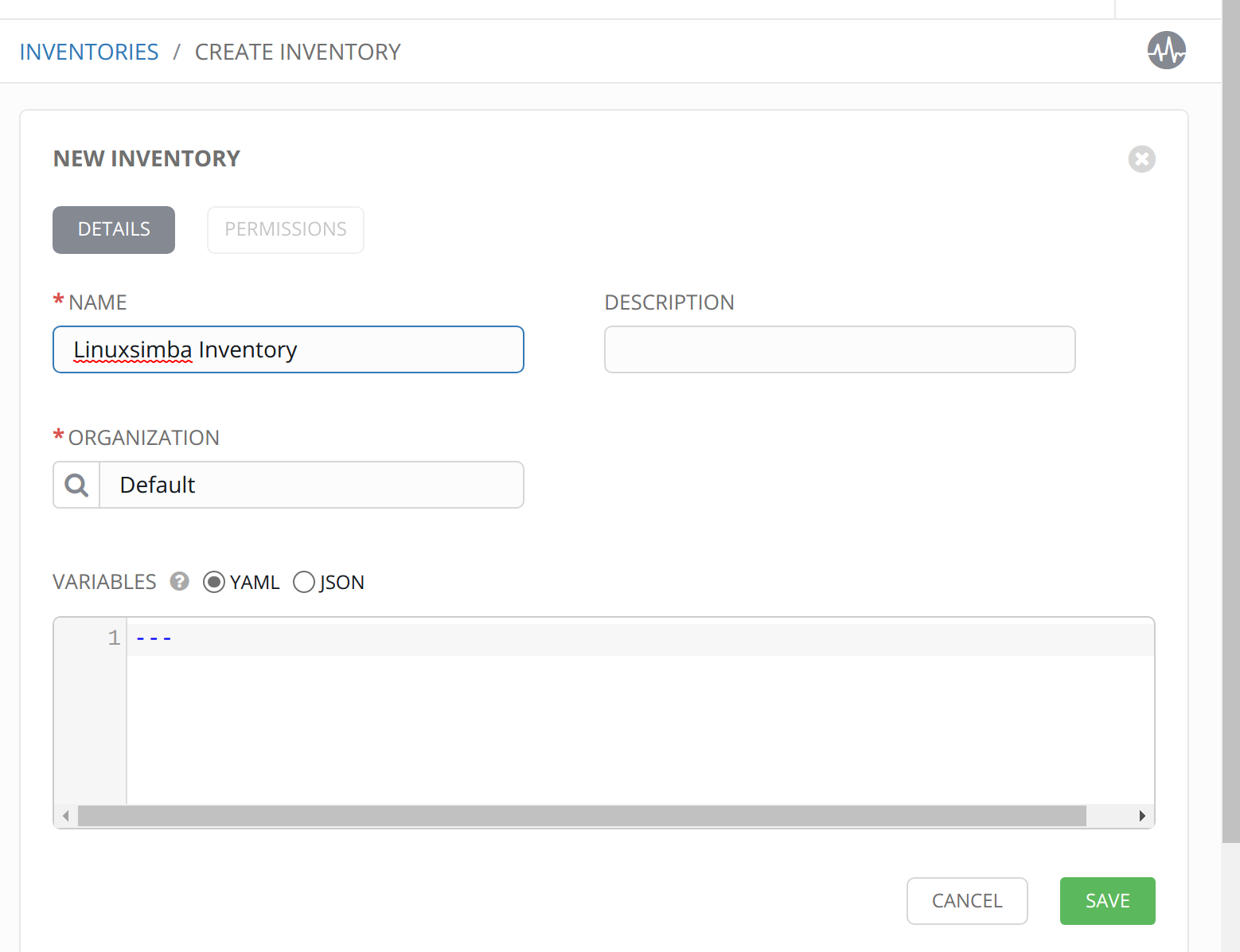
Create an Inventory
An inventory is a database of hosts and grouping of hosts that are referenced in the playbook. In the test playbook, the host group called switches is referenced. Tower will host this database so that the playbook just references it.
Create a Host Group
This step creates the switches host group. Hosts added with this group will execute the show version action in the tasks list of the text playbook.

Add Hosts to the Host Group
Only 1 network device is listed in this demo. It is called switch01 and its IP is 192.168.0.100. Note that the IP is defined in the variable ansible_host.

Create a Job Template
Create a object called a Job template. This brings together all the information entered before. For a network automation job, one creates a job template with an empty machine credential, a reference to a playbook. This playbook uses the local connection type, connection: local. Network authentication is set within the playbook and not in Tower using what Ansible Core (CLI) calls a network provider. In this case the provider is a variable hash called cli.

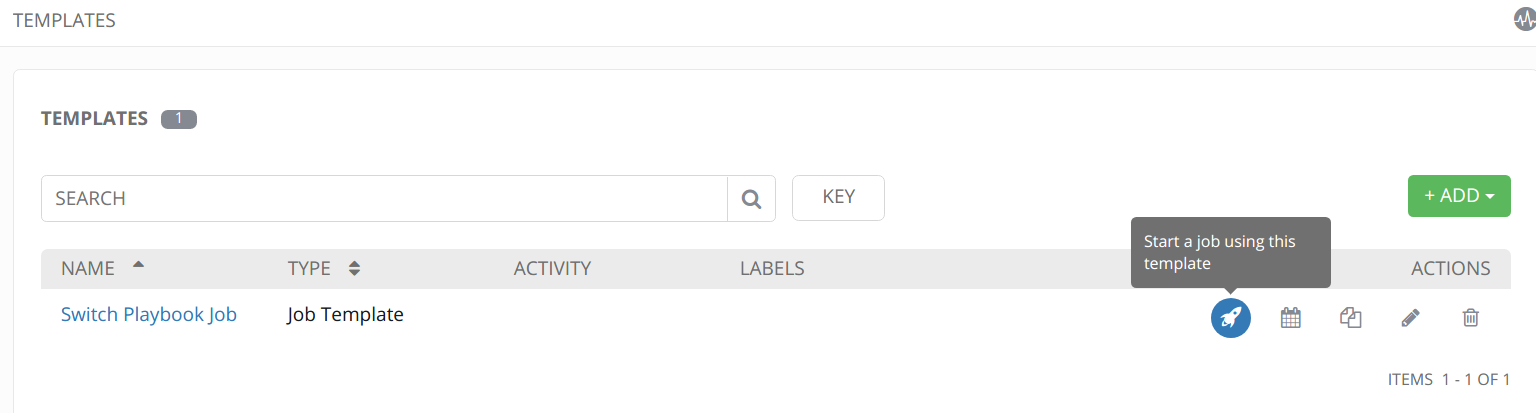
Run the Job Template
Finally run the job template. This creates what Tower calls a Job. Below are the results of executing the job.

Reference
- Test Network Automation Playbook
- Ansible Tower Installation Guide
- Ansible Tower Admin Reference Guide
- Network Device Authentication using Ansible 2.3
Written with StackEdit.
